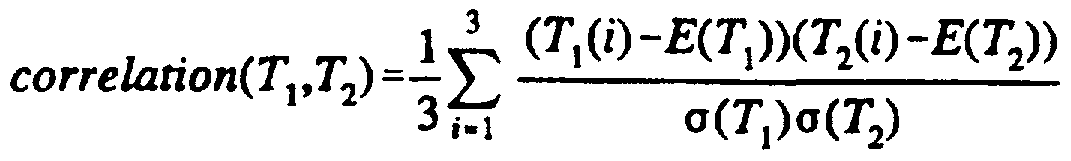WO1997023816A1 - User identification system for data processing equipment with keyboard - Google Patents
User identification system for data processing equipment with keyboard Download PDFInfo
- Publication number
- WO1997023816A1 WO1997023816A1 PCT/IB1996/001253 IB9601253W WO9723816A1 WO 1997023816 A1 WO1997023816 A1 WO 1997023816A1 IB 9601253 W IB9601253 W IB 9601253W WO 9723816 A1 WO9723816 A1 WO 9723816A1
- Authority
- WO
- WIPO (PCT)
- Prior art keywords
- keystrokes
- timings
- keystroke
- stored
- entered
- Prior art date
Links
Classifications
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/30—Authentication, i.e. establishing the identity or authorisation of security principals
- G06F21/31—User authentication
- G06F21/316—User authentication by observing the pattern of computer usage, e.g. typical user behaviour
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F21/00—Security arrangements for protecting computers, components thereof, programs or data against unauthorised activity
- G06F21/50—Monitoring users, programs or devices to maintain the integrity of platforms, e.g. of processors, firmware or operating systems
- G06F21/55—Detecting local intrusion or implementing counter-measures
- G06F21/554—Detecting local intrusion or implementing counter-measures involving event detection and direct action
-
- G—PHYSICS
- G06—COMPUTING; CALCULATING OR COUNTING
- G06F—ELECTRIC DIGITAL DATA PROCESSING
- G06F3/00—Input arrangements for transferring data to be processed into a form capable of being handled by the computer; Output arrangements for transferring data from processing unit to output unit, e.g. interface arrangements
- G06F3/01—Input arrangements or combined input and output arrangements for interaction between user and computer
- G06F3/02—Input arrangements using manually operated switches, e.g. using keyboards or dials
- G06F3/023—Arrangements for converting discrete items of information into a coded form, e.g. arrangements for interpreting keyboard generated codes as alphanumeric codes, operand codes or instruction codes
-
- G—PHYSICS
- G07—CHECKING-DEVICES
- G07C—TIME OR ATTENDANCE REGISTERS; REGISTERING OR INDICATING THE WORKING OF MACHINES; GENERATING RANDOM NUMBERS; VOTING OR LOTTERY APPARATUS; ARRANGEMENTS, SYSTEMS OR APPARATUS FOR CHECKING NOT PROVIDED FOR ELSEWHERE
- G07C9/00—Individual registration on entry or exit
- G07C9/30—Individual registration on entry or exit not involving the use of a pass
- G07C9/32—Individual registration on entry or exit not involving the use of a pass in combination with an identity check
- G07C9/33—Individual registration on entry or exit not involving the use of a pass in combination with an identity check by means of a password
Landscapes
- Engineering & Computer Science (AREA)
- Theoretical Computer Science (AREA)
- General Engineering & Computer Science (AREA)
- Computer Security & Cryptography (AREA)
- Physics & Mathematics (AREA)
- General Physics & Mathematics (AREA)
- Software Systems (AREA)
- Computer Hardware Design (AREA)
- General Health & Medical Sciences (AREA)
- Social Psychology (AREA)
- Health & Medical Sciences (AREA)
- Human Computer Interaction (AREA)
- Input From Keyboards Or The Like (AREA)
Abstract
User keystrokes and keystroke timings are continually captured during computer use. The captured keystrokes and timings are compared with a user profile of keystrokes and timings. A statistical analysis determines what should be in the profile and how the captured keystrokes and timings match up with the stored ones. An error action is initiated if the statistical analysis indicates that the user is not the one who is supposed to be using the computer.
Description
User identification system for data processing equipment with keyboard.
BACKGROUND OF THE INVENTION
The invention relates to the field of computer security and in particular to user identification.
In the past, a number of techniques have been proposed to improve computer security. For instance, passwords have been used to identify users as they sign on to computer systems.
Password techniques have the limitation that once a user signs on, there is no further checking as to the identity of the user. If the user leaves the computer without signing off, another user can come by and use the computer for nefarious purposes. To obviate this problem, some systems have screen saver software which puts a system into screen saver mode when a user has not been active on the computer and then require the user to enter a password to get out of the screen saver. However, since the screen saver takes some time to kick in, a crafty miscreant can still dart into a departed user's place and do his dastardly deeds. Another problem with password based systems, is that would-be intruders into the computer system may learn a password and enter that password in the genuine user's stead. Proposed solutions to this problem appear in R. J. Spillane, "Keyboard Apparatus for Personal Identification", IBM Tech. Disci. Bull. , vol. 17, No. 11 , April 1975 and GB 2,247,964A. Both of these systems propose looking at time intervals between key depressions during entry of a standard code or a password. These systems give some additional assurance that the password is being entered by the correct person, however, they still have the problem that, once a user is signed on, there is no additional verification.
SUMMARY OF THE INVENTION The object of the invention is improved user identification for computer security in keyboard based systems. The object is achieved in that keystrokes are continually analyzed to determine if they match stored sequences and to determine whether their timings match stored timings for the stored sequences.
BRIEF DESCRIPTION OF THE DRAWING
The invention will now be described by way of non-limitative example with reference to the following drawings.
Fig. 1 is a computer system equipped with the invention. Fig. 2 is a flowchart of an initialization routine for the invention.
Fig. 3 is a flowchart of a first embodiment of the invention.
Fig. 4 is a flowchart of a second embodiment of the invention.
DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS Fig. 1 shows a computer system on which the invention can run. The system includes equipment 101 to be guarded, which takes data from a keyboard 104. A user identification unit 105 processes data received from the equipment 101. The user identification unit 105 has a database 102 of security information. When data received from the equipment to be guarded 101 does not correlate with data in the database 102, the user identification unit 105 executes an error action 106. That action might be to lock the equipment 101 or to send an error message to another machine, for instance where a system administrator is sitting. The method can be run on a system where the user identification unit is incorporated within the equipment to be guarded. However, sometimes better security is achieved if the user identification unit is separate from the equipment to be guarded. Fig. 2 shows a flow chart of an initiation phase of the invention. During this phase, a database is created for a particular user. The user is asked to type a set of words or keystrokes. The words in the set should contain three letter sequences which are expected to be entered frequently by the user under actual operating conditions. The three letter sequences or triplets have been found to work well experimentally. However, sequences of other lengths could also be used.
The set could contain commonly used English words, or the list could contain commonly used computer commands or codes. For users of a UNIX based system, the set should preferably include commonly used UNIX operating system commands. Preferably the set should contain repetitions of the three letter sequences which are thought to be most useful, so that the user is given several opportunities to enter relevant triplets. In general the set should contain triplets which are "statistically repetitive". The term "statistically repetitive" will be defined below.
Block 200 starts the operation. So long as there are more words to type (201Y), the system analyzes input at 202. At 206, the computer orders the user to enter a word. The
loop 207/208 comprises the key-wise analyzing of the word, and the detecting whether the word has terminated effectively. The analyzing data include keystroke identifications and timings for each keystroke. Words are delimited by finding a sequence of keystrokes ending with a carriage return, a space, or a long time interval without keystrokes. The system then breaks the entered keystrokes for each word into triplets at
203. Each word can be represented by a set, (C(i) | 1 < i < the length of the word}, where C(i) is the i* character of this word. The keystroke timings for this word are represented by a set, {T(i) | 1 < i < length of the word}, where T(i) is the time lapsed between either entry of a previous keystroke or issuance of a system prompt, and - entry of the current keystroke.
A six letter word, for instance, will contain four triplets, {C(1),C(2),C(3)} , {C(2),C(3),C(4)}, {C(3),C(4),C(5)J , and (C(4),C(5),C(6)}. Each triplet is represented in the same form as the word, but the keystroke timings are converted into values relative to the time when the first character of this triplet is typed. Any words less than 3 characters is ignored by the system.
At 204, relevant timings are entered into the user's profile. The user profile should contain records of statistically repetitive triplets for that user.
When the list of words is complete, the system goes to block 209. Therein, for each statistically repetitive triplet (see 209), three mean values are stored 210 which represent means of the timings of the keystrokes for each character of that triplet. Also, for each statistically repetitive triplet, a variance value is stored 210 which represents a variance of the timings of all of the recorded keystrokes for that triplet. When all processing has finished, at 205, initialization ends.
Fig. 3 shows a flow chart of the operation of the invention after initialization. After start block 300, this flow chart is triggered by entry of a keystroke at 301. If a keystroke is detected, its identity and timing are captured at 302. Keystrokes are captured in sequence until a word is identified (see 303). The word is then broken into triplets, cf analogous operation at box 203 at Fig. 2. If, at 304, any of the triplets matches 310 a stored triplet developed in Fig. 2, the timings matched triplets are correlated with the timings of the stored triplets at 305. If no stored triplets are matched at 310, control returns to 301. Given two sets of keystroke timings (T,(i) | 1 < i < 3} and (T2(i) | 1 < i < 3} of the same triplet, the function E(x) denoting the mean of a variable x, and
the function σ(x) denoting the variance of a variable x, the correlation of the two sets of timings is given by
, and calculated in block 305.
Two keystroke timings are similar if the correlation between them is larger than a value close to 1 (e.g. 0.99). A triplet is "statistically repetitive" if the mean of the correlations of various versions of it is close to 1 (one) and the variance of correlations is small.
If the correlation exceeds a threshold at 306, control returns to 301. If the correlation does not exceed the threshold an error action can be commenced at 307 (cf box 106 of Fig. 1). Alternatively, the system could wait until the threshold has not been met several times before triggering an error action.
A statistically more reliable alternative is to trigger the error action after a series of correlation values fail to meet the threshold. In such an alternative, a number of yes or no votes is to be recorded with a list of most recently used words. If the ratio of yes to no votes is too small after a given number of matches, the error action would be triggered. Fig. 4 illustrates this alternative. If this is the first run since initialization per Fig. 2 after start block 400, at 401 a most recently used list must be initialized. The most recently used list should be initialized to some or all of the triplets in the personal profile, along with yes votes. During the running of the identity checker of the invention, the most recently used list will be updated. The most recently used list will be retained from session to session. After 401 , the steps of boxes 301 , 302, and 303, from Fig. 3 are executed. At
403 a retrieved word is broken into triplets and stored in the list. At 404, the system checks whether there are more triplets to check in the list. If no, control returns to 402. If yes, at 405, the system tests whether the current triplet is in the user's personal profile. If so, the most recently used list is updated at 406. The method of updating the most recently used list will be explained below. Then at 407, the correlation of the current triplet is calculated as per the above equation. Then, as a result of the correlation calculation, "yes" and "no" votes are updated at 408. Updating of "yes" and "no" votes will be explained below together with the explanation for the updating of the most recently used list.
At 409, the system calculates whether a ratio of "yes" to "no" votes exceeds a threshold. If not, the error action 307 is triggered. If so, the current triplet is deleted from
410 and control is returned to 404. The threshold can be any ratio which works in practice. A ratio of 80% was found to work in one experiment.
Updating of the most recently used list and the "yes/no" votes will now be explained. The idea is to keep a running count of whether the user is typing as expected. Therefore several values must be compared. Below, the variable T represents a current time and the variable N represents the length of the list of most recently used triplets. The variable N can take on any value which works in practice. In one experiment, a value of 20 for N was found to give reasonable results. At time T, the N most recently used triplets list might look like the following.
Triplet Time for the most recent "yes" or "no" appearance
triplet j T-100 sec yes
triplet2 T-95 sec yes
triplet3 T-92 sec no
• • •
tripletN T- 10 sec yes
When tripletN+ j is entered, the system has to check whether the new triplet is in the most recently used list. If not, the update will take the following form.
Triplet Time for the most recent "yes" or "no" appearance
triplet2 T-95 sec yes
triplet3 T-92 sec no
• • •
tripletN T-10 sec yes
tripletN+ 1 T sec no
In other words, the oldest triplet is removed from the list, and the most recent one is added. The second column of this table is updated at 406, while the third column is updated at 408. If, on the other hand, the newest triplet already appears in the list, a different type of updating is undertaken. If for instance the tripletN= ] =triplet3, the list will look as follows:
Triplet Time "yes" or "no"
triplet! T-100 sec yes
triplet2 T-95 sec yes
triplet4 T-85 sec yes
• • •
tripletN T-10 sec yes
In this way, there are always N triplets in the most recently used list, and there are no duplicate triplets in the list. Yet another alternative would be to establish multiple yes/no ratio thresholds. In such a case, the error action would be initiated either if a small number of correlations gave highly aberrant values; or a larger number of correlations gave slightly aberrant values. Sometimes user patterns of typing vary over time. For instance, as a user
becomes more experienced, the timings will decrease. If a user acquires new software, the sequences of keystrokes that are statistically repetitive may change. Therefore, it may be desirable to allow the system to update user profiles over time.
Claims
1. A computer method for identifying a computer user, the method comprising the following steps receiving user data at a keyboard; continually seeking to match entered sequences of keystrokes with stored predetermined sequences of keystrokes; continually capturing entered keystroke timings; comparing particular entered keystroke timings, in a sequence of entered keystrokes that matches one stored predetermined sequence of keystrokes; and - stored keystroke timings that correspond to the one stored predetermined sequence of keystrokes; and executing an error action when the particular entered keystroke timings fail to compare properly with the stored keystroke timings.
2. The method of claim 1 wherein comparing comprises using a statistical formula to analyze a statistical likelihood that the particular entered keystroke timings were entered by a same use as the stored keystroke timings corresponding to the one stored predetermined sequence of keystrokes.
3. The method of claim 1 wherein the statistical formula is
where - i is an index running from one to three;
Tj(i) is the x^1 particular entered keystroke timing;
T2(i) is an average value of timings of the ith keystroke taken during an initialization phase and corresponding to the one stored predetermined sequence of keystrokes; - E(Tj) is the mean of the Tι(i) values;
E(T2) is the mean of the T2(i) values; σ(T]) is the variance of the T,(i) values; <x(T2) is the variance of the T2(i) values.
4. The method of claim 3 wherein the particular entered keystroke timings are considered to match when correlation(Tj ,T2) exceeds a predetermined threshold.
5. The method of claim 4 wherein the threshold is E-0.5σ, where E is the mean of the keystroke timings for the one stored predetermined sequence of keystrokes and σ is the variance of the keystroke timings for the one stored predetermined sequence of keystrokes.
6. The method as claimed in any of claims 1 to 5, wherein the error action is triggered after several failures of entered keystroke timings to compare properly with stored keystroke timings.
7. The method as claimed in any of claims 1 to 6 further comprising the step of maintaining a list of recently used sequences of keystrokes; and wherein executing the error action comprises only executing the error action when a number of sequences of keystrokes in the list, which compared properly with the stored keystroke timings, fails to meet a predetermined threshold.
8. A computer system comprising a processor; a keyboard; - means for, in response to data entered by a user on the keyboard, continually seeking to match entered sequences of keystrokes with stored predetermined sequences of keystrokes; and continually capturing entered keystroke timings; means for comparing - particular entered keystroke timings, in a sequence of entered keystrokes that matches one stored predetermined sequence of keystrokes; and stored keystroke timings that correspond to the one stored predetermined sequence of keystrokes; and code means for executing an error action when the particular entered keystroke timings fail to compare properly with the stored keystroke timings.
9. The system of claim 8 wherein the comparing means comprises statistical formula means for analyzing a statistical likelihood that the particular entered keystroke timings were entered by a same user as the stored keystroke timings corresponding to the one stored predetermined sequence of keystrokes.
10. The system of claim 9 wherein the statistical likelihood is analyzed according to the following formula
where i is an index running from one to three; - Tj(i) is the ith particular entered keystroke timing;
T2(i) is an average value of timings of the iΛ keystroke taken during an initialization phase and corresponding to the one stored predetermined sequence of keystrokes;
E(T]) is the mean of the T, (i) values; - E(T2) is the mean of the T2(i) values; σ(T,) is the variance of the T,(i) values; σ(T2) is the variance of the T2(i) values.
11. The system of claim 10 wherein the particular entered keystroke timings are considered to match when correlation(Tι ,T2) exceeds a predetermined threshold.
12. The system of claim 10 wherein the threshold is E-0.5σ, where E is the mean of the keystroke timings for the one stored predetermined sequence of keystrokes and σ is the variance of the keystroke timings for the one stored predetermined sequence of keystrokes.
13. The system as claimed in any of claims 8 to 12 wherein the error action is triggered after several failures of entered keystroke timings to compare properly to stored keystroke timings.
14. The system as claimed in any of claims 8 to 13 further comprising means for maintaining a list of recently used sequences of keystrokes; and wherein the means for executing the error action only executes the error action when a number of sequences of keystrokes in the list, which compared properly with the stored keystroke timings, fails to meet a predetermined threshold.
Applications Claiming Priority (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US57610595A | 1995-12-21 | 1995-12-21 | |
| US08/576,105 | 1995-12-21 |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| WO1997023816A1 true WO1997023816A1 (en) | 1997-07-03 |
Family
ID=24303012
Family Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| PCT/IB1996/001253 WO1997023816A1 (en) | 1995-12-21 | 1996-11-19 | User identification system for data processing equipment with keyboard |
Country Status (1)
| Country | Link |
|---|---|
| WO (1) | WO1997023816A1 (en) |
Cited By (20)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| EP1470549A1 (en) * | 2001-12-12 | 2004-10-27 | International Business Machines Corporation | Method and system for non-intrusive speaker verification using behavior models |
| EP1512113A2 (en) * | 2002-05-15 | 2005-03-09 | Biocom, LLC | Identity verification system |
| GB2413425A (en) * | 2004-04-23 | 2005-10-26 | Hewlett Packard Development Co | Biometric analysis method |
| DE102004049428A1 (en) * | 2004-10-08 | 2006-04-20 | Claudia Von Heesen | Automatic identification and verification of user data to provide access by a user to electronic equipment |
| FR2878344A1 (en) * | 2004-11-22 | 2006-05-26 | Sionnest Laurent Guyot | DATA CONTROLLER AND INPUT DEVICE |
| FR2878343A1 (en) * | 2004-11-22 | 2006-05-26 | Tiki Systems Soc Par Actions S | Data input and control device e.g. combinatorial keyboard, for e.g. computer system, has three main detection zones associated to respective index, middle and ring fingers of hand, where each zone has front and rear logical sensitive zones |
| EP2069993A2 (en) * | 2006-10-04 | 2009-06-17 | Behaviometrics AB | Security system and method for detecting intrusion in a computerized system |
| US7689418B2 (en) | 2000-03-01 | 2010-03-30 | Nuance Communications, Inc. | Method and system for non-intrusive speaker verification using behavior models |
| US10489772B2 (en) | 2013-11-27 | 2019-11-26 | At&T Intellectual Property I, L.P. | Out-of-band device verification of transactions |
| US11238456B2 (en) * | 2003-07-01 | 2022-02-01 | The 41St Parameter, Inc. | Keystroke analysis |
| WO2022067436A1 (en) * | 2020-09-30 | 2022-04-07 | Mastercard Technologies Canada ULC | User identification with input profile record |
| US11410179B2 (en) | 2012-11-14 | 2022-08-09 | The 41St Parameter, Inc. | Systems and methods of global identification |
| US11657299B1 (en) | 2013-08-30 | 2023-05-23 | The 41St Parameter, Inc. | System and method for device identification and uniqueness |
| US11683306B2 (en) | 2012-03-22 | 2023-06-20 | The 41St Parameter, Inc. | Methods and systems for persistent cross-application mobile device identification |
| US11683326B2 (en) | 2004-03-02 | 2023-06-20 | The 41St Parameter, Inc. | Method and system for identifying users and detecting fraud by use of the internet |
| US11727471B2 (en) | 2006-03-31 | 2023-08-15 | The 41St Parameter, Inc. | Systems and methods for detection of session tampering and fraud prevention |
| US11750584B2 (en) | 2009-03-25 | 2023-09-05 | The 41St Parameter, Inc. | Systems and methods of sharing information through a tag-based consortium |
| US11886575B1 (en) | 2012-03-01 | 2024-01-30 | The 41St Parameter, Inc. | Methods and systems for fraud containment |
| US11895204B1 (en) | 2014-10-14 | 2024-02-06 | The 41St Parameter, Inc. | Data structures for intelligently resolving deterministic and probabilistic device identifiers to device profiles and/or groups |
| US11907350B2 (en) | 2020-09-30 | 2024-02-20 | Mastercard Technologies Canada ULC | User identification with blended response from dual-layer identification service |
Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4621334A (en) * | 1983-08-26 | 1986-11-04 | Electronic Signature Lock Corporation | Personal identification apparatus |
| US4805222A (en) * | 1985-12-23 | 1989-02-14 | International Bioaccess Systems Corporation | Method and apparatus for verifying an individual's identity |
| GB2247964A (en) * | 1990-09-13 | 1992-03-18 | John Robert Devany | Controlling access to a keyboard-operated computer system |
-
1996
- 1996-11-19 WO PCT/IB1996/001253 patent/WO1997023816A1/en active Application Filing
Patent Citations (3)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US4621334A (en) * | 1983-08-26 | 1986-11-04 | Electronic Signature Lock Corporation | Personal identification apparatus |
| US4805222A (en) * | 1985-12-23 | 1989-02-14 | International Bioaccess Systems Corporation | Method and apparatus for verifying an individual's identity |
| GB2247964A (en) * | 1990-09-13 | 1992-03-18 | John Robert Devany | Controlling access to a keyboard-operated computer system |
Non-Patent Citations (1)
| Title |
|---|
| IBM TECHNICAL DISCLOSURE BULLETIN, Volume 17, No. 11, April 1975, R.J. SPILLANE, "Keyboard Apparatus For Personal Identification". * |
Cited By (29)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US7689418B2 (en) | 2000-03-01 | 2010-03-30 | Nuance Communications, Inc. | Method and system for non-intrusive speaker verification using behavior models |
| EP1470549A1 (en) * | 2001-12-12 | 2004-10-27 | International Business Machines Corporation | Method and system for non-intrusive speaker verification using behavior models |
| EP1470549A4 (en) * | 2001-12-12 | 2007-08-08 | Ibm | Method and system for non-intrusive speaker verification using behavior models |
| EP1512113A4 (en) * | 2002-05-15 | 2008-10-29 | Biocom Llc | Identity verification system |
| EP1512113A2 (en) * | 2002-05-15 | 2005-03-09 | Biocom, LLC | Identity verification system |
| US11238456B2 (en) * | 2003-07-01 | 2022-02-01 | The 41St Parameter, Inc. | Keystroke analysis |
| US11683326B2 (en) | 2004-03-02 | 2023-06-20 | The 41St Parameter, Inc. | Method and system for identifying users and detecting fraud by use of the internet |
| GB2413425A (en) * | 2004-04-23 | 2005-10-26 | Hewlett Packard Development Co | Biometric analysis method |
| GB2413425B (en) * | 2004-04-23 | 2008-04-09 | Hewlett Packard Development Co | Biometric analysis system, methods, apparatus and software using biometric analysis |
| DE102004049428A1 (en) * | 2004-10-08 | 2006-04-20 | Claudia Von Heesen | Automatic identification and verification of user data to provide access by a user to electronic equipment |
| WO2006053991A1 (en) * | 2004-11-22 | 2006-05-26 | Laurent Guyot-Sionnest | Method and device for controlling and inputting data |
| FR2878343A1 (en) * | 2004-11-22 | 2006-05-26 | Tiki Systems Soc Par Actions S | Data input and control device e.g. combinatorial keyboard, for e.g. computer system, has three main detection zones associated to respective index, middle and ring fingers of hand, where each zone has front and rear logical sensitive zones |
| US8125440B2 (en) | 2004-11-22 | 2012-02-28 | Tiki'labs | Method and device for controlling and inputting data |
| FR2878344A1 (en) * | 2004-11-22 | 2006-05-26 | Sionnest Laurent Guyot | DATA CONTROLLER AND INPUT DEVICE |
| US11727471B2 (en) | 2006-03-31 | 2023-08-15 | The 41St Parameter, Inc. | Systems and methods for detection of session tampering and fraud prevention |
| US8443443B2 (en) | 2006-10-04 | 2013-05-14 | Behaviometrics Ab | Security system and method for detecting intrusion in a computerized system |
| EP2069993A4 (en) * | 2006-10-04 | 2011-05-18 | Behaviometrics Ab | Security system and method for detecting intrusion in a computerized system |
| EP2069993A2 (en) * | 2006-10-04 | 2009-06-17 | Behaviometrics AB | Security system and method for detecting intrusion in a computerized system |
| US11750584B2 (en) | 2009-03-25 | 2023-09-05 | The 41St Parameter, Inc. | Systems and methods of sharing information through a tag-based consortium |
| US11886575B1 (en) | 2012-03-01 | 2024-01-30 | The 41St Parameter, Inc. | Methods and systems for fraud containment |
| US11683306B2 (en) | 2012-03-22 | 2023-06-20 | The 41St Parameter, Inc. | Methods and systems for persistent cross-application mobile device identification |
| US11410179B2 (en) | 2012-11-14 | 2022-08-09 | The 41St Parameter, Inc. | Systems and methods of global identification |
| US11922423B2 (en) | 2012-11-14 | 2024-03-05 | The 41St Parameter, Inc. | Systems and methods of global identification |
| US11657299B1 (en) | 2013-08-30 | 2023-05-23 | The 41St Parameter, Inc. | System and method for device identification and uniqueness |
| US11423388B2 (en) | 2013-11-27 | 2022-08-23 | At&T Intellectual Property I, L.P. | Out-of-band device verification of transactions |
| US10489772B2 (en) | 2013-11-27 | 2019-11-26 | At&T Intellectual Property I, L.P. | Out-of-band device verification of transactions |
| US11895204B1 (en) | 2014-10-14 | 2024-02-06 | The 41St Parameter, Inc. | Data structures for intelligently resolving deterministic and probabilistic device identifiers to device profiles and/or groups |
| WO2022067436A1 (en) * | 2020-09-30 | 2022-04-07 | Mastercard Technologies Canada ULC | User identification with input profile record |
| US11907350B2 (en) | 2020-09-30 | 2024-02-20 | Mastercard Technologies Canada ULC | User identification with blended response from dual-layer identification service |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| WO1997023816A1 (en) | User identification system for data processing equipment with keyboard | |
| US7802103B2 (en) | Key sequence rhythm recognition system and method | |
| Umphress et al. | Identity verification through keyboard characteristics | |
| US8079061B2 (en) | Authentication system managing method | |
| US7305559B2 (en) | Software method for improved password entry | |
| US8020005B2 (en) | Method and apparatus for multi-model hybrid comparison system | |
| US6895514B1 (en) | Method and apparatus for achieving secure password access | |
| US5420936A (en) | Method and apparatus for accessing touch screen desktop objects via fingerprint recognition | |
| Syukri et al. | A user identification system using signature written with mouse | |
| KR19990009965A (en) | User authentication method using typing pattern | |
| JP6511293B2 (en) | User monitoring system | |
| JP2001092783A (en) | Method and system for personal authentication, and recording medium | |
| EP1873675A2 (en) | Biometric authentication method and system | |
| JPS62157966A (en) | Method and apparatus for checking identity of person | |
| Bours et al. | A login system using mouse dynamics | |
| US20080028231A1 (en) | Key sequence trustable activation recognition system and method | |
| JP2001516474A (en) | User identification confirmation method for data processing device that generates alphabetic characters by keyboard operation | |
| CN106778151A (en) | Method for identifying ID and device based on person's handwriting | |
| US20080034218A1 (en) | Key sequence rhythm guidance recognition system and method | |
| JPH10154231A (en) | Person authentication device using biometrics information and method therefor | |
| US20080133933A1 (en) | Key sequence rhythm recognition system and method | |
| EP2490149A1 (en) | System for verifying user identity via mouse dynamics | |
| Siahaan et al. | Spoofing keystroke dynamics authentication through synthetic typing pattern extracted from screen-recorded video | |
| US20080028232A1 (en) | Key sequence recognition and password hardening system and method | |
| CN113407921B (en) | Handwriting recognition login method |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AK | Designated states |
Kind code of ref document: A1 Designated state(s): JP |
|
| AL | Designated countries for regional patents |
Kind code of ref document: A1 Designated state(s): AT BE CH DE DK ES FI FR GB GR IE IT LU MC NL PT SE |
|
| 121 | Ep: the epo has been informed by wipo that ep was designated in this application | ||
| 122 | Ep: pct application non-entry in european phase | ||
| NENP | Non-entry into the national phase |
Ref country code: JP Ref document number: 97523449 Format of ref document f/p: F |