Last update: April 15, 2024
Background
Windows uses a simple technique to recognize which files were downloaded from the Internet (or a network share).
Each downloaded file is is tagged with a hidden NTFS Alternate Data Stream file named Zone.Identifier. You can check for the presence of this “Mark of the Web” (MotW) using dir /r or programmatically, and you can view the contents of the MotW stream using Notepad:

Within the file, the ZoneTransfer element contains a ZoneId element with the ordinal value of the URLMon Zone from which the file came1. The value 3 indicates that the file is from the Internet Zone2.
Aside: One common question is “Why does the file contain a Zone Id rather than the original URL? There’s a lot of cool things that we could do if a URL was preserved!” The answer is mostly related to privacy—storing a URL within a hidden data stream is a foot gun that would likely lead to accidental disclosure of private URLs. This problem isn’t just theoretical—the Alternate Data Stream is only one mechanism used for MotW. Another mechanism involves writing a <!--saved from url=http://example.com> comment to HTML markup; that form does include a raw URL. A few years ago, attackers noticed that they could use Google to search for files containing a MOTW of the form <!--saved from url(0042)ftp://username:secretpassword@host.com –> and collect credentials. Oops. Update: Microsoft apparently decided the tradeoff was worth it. Windows 10+ includes the referrer URL, source URL and other information.
Browsers and other internet clients (e.g. email and chat programs) can participate in the MOTW-marking system by using the IAttachmentExecute interface’s methods or by writing the Alternate Data Stream directly. Chrome uses IAttachmentExecute and thus includes the URL information on Windows 10. Firefox writes the Alternate Data Stream directly (and as of February 2021, it too includes the URL information).
Handling Marked Files
The Windows Shell and some applications treat files with a Mark-of-the-Web differently than those without. For instance, examining a downloaded executable file’s properties shows the following notice:

More importantly, attempting to run the executable using Windows Explorer or ShellExecute() will first trigger evaluation using SmartScreen Application Reputation (Win8+) and any registered anti-virus scanners. The file’s digital signature will be checked, and execution will be confirmed with the user, either using the older Attachment Execution Services prompt, or the newer UAC elevation prompt:
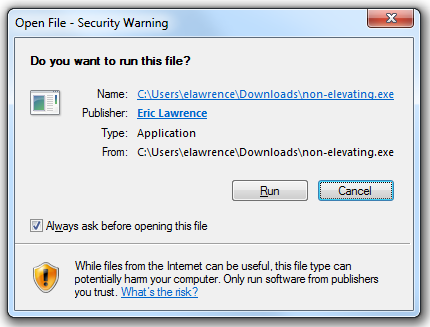

Notably, MotW files invoked by non-shell means (e.g. cmd.exe or PowerShell) do not trigger security checks or prompts. Additionally, while SmartScreen only checks the reputation Windows 11’s Smart App Control goes further than SmartScreen and evaluates trust/signatures of all code (DLLs, scripts, etc) that is loaded by the Windows OS Loader and script engines.
Microsoft Office documents bearing a MotW open in Protected View, a security sandbox that attempts to block many forms of malicious content, and starting in 2022, macros are disabled in Internet-sourced documents.
Trivia: Some applications inherit protections against files bearing a MotW, but don’t have any user-interface that explains what is going on. For instance, if you download a CHM with a MotW, its HTML content will not render until you unblock it using the “Always ask before opening this file” or the “Unblock” button:

What Could Go Wrong?
With such a simple scheme, what could go wrong? Unfortunately, quite a lot.
Internet Clients must participate
The first hurdle is that Internet clients must explicitly mark their downloads using the Mark-of-the-Web, either by calling IAttachmentExecute or by writing the Alternate Data Stream directly. Most popular clients will do so, but support is neither universal nor comprehensive.
For instance, for a few years, Firefox failed to mark downloads if the user used the Open command instead of Save.
In other cases, some browser plugins may allow attackers to save files to disk and bypass MotW tagging.
Microsoft Outlook (tested v2010) and Microsoft Windows Live Mail Desktop (tested v2012 16.4.3563.0918) both tag message attachments with a MotW you double-click on an attachment or right-click and choose Save As. Unfortunately, however, both clients fail to tag attachments if the user uses drag-and-drop to copy the attachment to somewhere in their filesystem. This oversight is likely to be seen in many different clients, owing to the complexity in determining the drop destination.
There are many ways to download files to a Windows system that do not result in writing a MotW to the file. For example, you can use the copy of CURL that ships in modern Windows 11, you can have a script that calls into WinINET or WinHTTP or System.NET objects, or you can use any of various binaries that offer downloads as a side-effect.
Target file system must be NTFS
The Zone.Identifier stream can only be saved in an NTFS stream. These streams are not available on FAT32-formatted devices (e.g. some USB Flash drives), CD/DVDs, or the ReFS file system in Windows 8 / Server 2012 (support was later added to ReFS in Windows 8.1).
If you copy a file tagged with a MotW to a non-NTFS filesystem (or try to save it to such a file system to start with), the Mark of the Web is omitted and the protection is lost.
Originating location must be Internet or Restricted Zone
The IAttachmentExecute:Save API will not write the MotW unless the URL provided in the SetSource method is in a zone configured to write it (e.g. Trusted, Internet or Restricted Sites zone).

On some systems, code may have added domains to the user’s Trusted Sites zone without their knowledge.
On other systems, a proxy configuration script may cause Internet sites to be treated as belonging to the Intranet zone.
The Attachment Execution Services API also will not write a MoTW to a download if that Zone’s setting for Launching applications and unsafe files is set to Enable.
Normally, Windows will howl if this unsafe configuration is set for the Internet Zone, but there’s a registry key that turns off the “Your security settings are unsafe” warning bar:

Policy must not disable the feature
Writing of the MoTW can be suppressed in the AttachmentExecuteServices API via Group Policy. In GPEdit.msc, see Administrative Templates > Windows Components > Attachment Manager > Do not preserve zone information in file attachments
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments]SaveZoneInformation
A value of 1 will prevent the MoTW from being written to files.
Source scheme must be HTTP/HTTPS/FILE/FTP-like
Some sites use scripts to generate file downloads that don’t have a traditional source URL.
If the source of the download is a data: URI, for example, the browser has no great way to know what marking to put on the file. For data URIs or other anonymous sources, writing a default of about:internet is a common conservative choice to ensure that the file was treated as if it came from the Internet Zone. Similarly, about:untrusted causes the file to be treated as originating from the Restricted Sites Zone.
blob: scheme URIs have a similar issue, but because blob URIs only exist within a security context (https://example/download/file.aspx can create blob:https://example/guid) the client can write that security context’s origin as a URL (e.g. https://example/ in this case) into the MoTW to help ensure proper handling.
Origin Laundering via Archives
One simple trick that attackers use to try to circumvent MotW protections is to enclose their data within an archive like a .ZIP, .7z, or .RAR file, or a virtual disk like a .iso file. Attackers may go further and add a password to block virus scanners; the password is provided to the victim in the attacking webpage or email.
In order to remain secure, archive extractors must correctly propagate the MotW from the archive file itself to each file extracted from the archive.
Despite being one of the worst ZIP clients available, Windows Explorer gets this right:

In contrast, 7-zip does not reliably get this right. Malware within a 7-zip archive can be extracted without propagation of the MotW. 7-zip v15.14 will add a MotW if you double-click an exe within an archive, but not if you extract it first. The older 7-zip v9.2 did not tag with MotW either way.
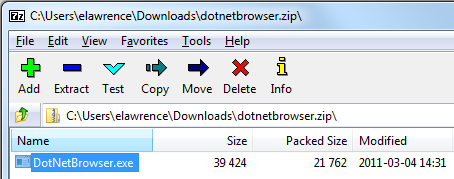
A quick look at popular archive extractors shows:
- Windows Explorer – Not vulnerable
- WinRar 5.31 – Not vulnerable
- WinZip 20.0.11649 – Not vulnerable
- 7-Zip 15.14 – Vulnerable (bug); 7-Zip 22.0 – Optional
- IZArc 4.2 – Vulnerable (Developer says: “Will be fixed in next version“)
Update: A researcher has surveyed the current MoTW-propagation landscape as of May 2022.
SmartScreen & the User may unmark
Finally, users may unmark files using the Unblock button on the file’s Properties dialog in Windows Explorer, or by unticking the “Always ask before opening this file” checkbox on the pre-launch security prompt.
Similarly, on systems with Microsoft SmartScreen, SmartScreen itself may unmark the file (actually, it replaces the ZoneId with an (undocumented) field of AppZoneId=4) Update March 2022: SmartScreen now seems to have changed to write a separate SmartScreen alternate stream from Edge, rather than modifying the Zone.Identifier stream. Update Feb 2023: When executing a program from the Windows Shell in Win11, the Zone.Identifier stream is removed from the file after the AppRep check.
Mark-of-the-Web is valuable, but fragile.
Dec 2022 Update: I’ve written a new post containing guidance for implementers using MoTW.
-Eric Lawrence
Appendix: Useful Scripts
It is sometimes nice to be able to set and view the Mark-of-the-Web data streams from the command line. Create three text files in C:\tools like so:
motw.cmd
@dir /r "%1"
@echo.
@echo == Alternate Data Stream ==
@echo.
@more < "%1:Zone.Identifier"
MOTWTag.cmd
@type C:\tools\InternetZoneADS.txt > "%1:Zone.Identifier"
InternetZoneADS.txt
[ZoneTransfer]
ZoneId=3
1 This is an oversimplification. The ZoneId value written is the least-privileged zone of the calculated zones for the caller-supplied Source URL and the Referrer URL. Interestingly, this means that if you download a Trusted Zone file from a link on an Internet Zone webpage, it will be treated as if it had originated from the Internet Zone.
There are other (surprising) nuances as well.
First, if either the Source or Referrer is not supplied, it is treated as “Local Machine Zone”; a caller can pass about:internet as a generic “Internet Zone” URL, or about:untrusted as a generic “Restricted Sites” URL. Using a generic URL can be necessary if the file is sourced from a non-basic URL like blob: or one that is over 2083 characters (INTERNET_MAX_URL_LENGTH).
Second, the determination of what zone is “least-privileged” diverges from the standard order for Windows Security Zones. The MoTW code orders the Zones as Untrusted < Internet < Intranet < Local Machine < Trusted. The standard ordering in URLMon is Untrusted < Internet < Trusted < Intranet < Local Machine
Third, the Zone Marking code is hard-coded to avoid writing a MoTW to a file whose “least-privileged” zone is Local Machine. This seems reasonable (otherwise copying a file from the local computer to the local computer could add a MoTW), but, coupled with the non-standard ordering of Zones, results in a surprising outcome. To wit, if you call the API with a Source URL in the Trusted Zone, but do not supply a Referrer URL (say, because the user entered the URL in the address bar, or the download link has a rel=noreferrer attribute), no MoTW is written to the file (test case).
2 The Windows Zone identifier constants are Restricted Zone=4, Internet=3, Trusted Zone=2, Intranet=1. The Local Machine Zone is 0, but the API will not write a Zone.Identifier stream for a file whose ZoneId is 0.


Interesting! Thanks for sharing. Did you happen to file bugs against 7-Zip and IZArc?
7-Zip’s bug is now linked. I used IZArc’s “Contact Us” link, but I didn’t see a public bug tracker.
Is the UAC prompt only triggered in place of the AES prompt whenever the executable needs to elevate or are there other variables? Another neat security-related thing that Microsoft could do is updated and include the File Checksum Integrity Verifier tool with Windows.
https://support.microsoft.com/en-us/kb/841290
https://www.microsoft.com/en-us/download/details.aspx?id=11533
I know there are FOSS tools like the *sum set (md5sum, sha1sum, etc.) and HashCheck but a native OS tool with both console and graphical UIs benefits everyone.
UAC replaces the Attachment Execution Services prompt only when elevating.
Windows can natively calculate file hashes via
certutil.exe -hashfile c:\Windows\system32\notepad.exe [MD2 MD4 MD5 SHA1 SHA256 SHA384 SHA512]but this is only useful if the expected hash is securely communicated (and you are able to validate the sender). Authenticode helps resolve both of those challenges.I tested it with the venerable Info-Zip unzip program (from cygwin) and it doesn’t propagate the MotW.
Writing of the MoTW can be suppressed in the AttachmentExecuteServices API via
GPEdit.msc > Administrative Templates > Windows Components > Attachment Manager > “Do not preserve zone information in file attachments”
[HKEY_CURRENT_USER \Software \Microsoft \Windows \CurrentVersion\Policies \Attachments]
SaveZoneInformation = 1 (On = 1, Off = 2)
Hi, ReFS does support MOTW or zone.identifiers. files downloaded and copied to volumes with ReFS filesystem retain those information. I just tested it on the latest version of Windows 11.
`Get-Content -stream zone.identifier`
They do get lost when copied to FAT32 formatted filesystems though.
Thanks, I’ve updated the post.
Thanks, btw sorry about posting the comment 3 times, couldn’t see if my comment was successfully posting probably bcz of 3rd party cookie blocking :)
also there is a fork of 7zip called Nanazip that supports MOTW and is digitally signed https://www.microsoft.com/store/productId/9N8G7TSCL18R